Page 29 - REC :: M.E. EST Curriculum and Syllabus - R2019
P. 29
M.E Embedded System Technologies
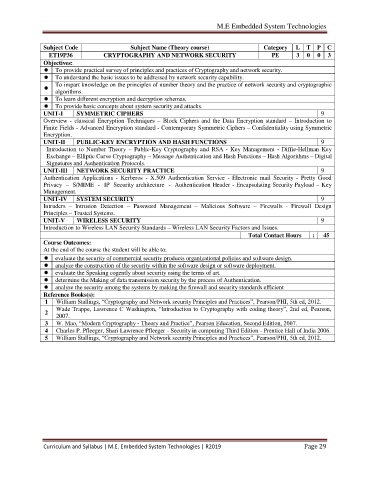
Subject Code Subject Name (Theory course) Category L T P C
ET19P36 CRYPTOGRAPHY AND NETWORK SECURITY PE 3 0 0 3
Objectives:
To provide practical survey of principles and practices of Cryptography and network security.
To understand the basic issues to be addressed by network security capability.
To impart knowledge on the principles of number theory and the practice of network security and cryptographic
algorithms.
To learn different encryption and decryption schemas.
To provide basic concepts about system security and attacks.
UNIT-I SYMMETRIC CIPHERS 9
Overview - classical Encryption Techniques – Block Ciphers and the Data Encryption standard – Introduction to
Finite Fields - Advanced Encryption standard - Contemporary Symmetric Ciphers – Confidentiality using Symmetric
Encryption.
UNIT-II PUBLIC-KEY ENCRYPTION AND HASH FUNCTIONS 9
Introduction to Number Theory – Public-Key Cryptography and RSA - Key Management - Diffie-Hellman Key
Exchange – Elliptic Curve Cryptography – Message Authentication and Hash Functions – Hash Algorithms – Digital
Signatures and Authentication Protocols.
UNIT-III NETWORK SECURITY PRACTICE 9
Authentication Applications - Kerberos - X.509 Authentication Service - Electronic mail Security - Pretty Good
Privacy – S/MIME - IP Security architecture - Authentication Header - Encapsulating Security Payload – Key
Management.
UNIT-IV SYSTEM SECURITY 9
Intruders – Intrusion Detection – Password Management – Malicious Software – Firewalls - Firewall Design
Principles – Trusted Systems.
UNIT-V WIRELESS SECURITY 9
Introduction to Wireless LAN Security Standards – Wireless LAN Security Factors and Issues.
Total Contact Hours : 45
Course Outcomes:
At the end of the course the student will be able to:
evaluate the security of commercial security products organizational policies and software design.
analyze the construction of the security within the software design or software deployment.
evaluate the Speaking cogently about security using the terms of art.
determine the Making of data transmission security by the process of Authentication.
analyse the security among the systems by making the firewall and security standards efficient
Reference Books(s):
1 William Stallings, “Cryptography and Network security Principles and Practices”, Pearson/PHI, 5th ed, 2012.
Wade Trappe, Lawrence C Washington, “Introduction to Cryptography with coding theory”, 2nd ed, Pearson,
2
2007.
3 W. Mao, “Modern Cryptography - Theory and Practice”, Pearson Education, Second Edition, 2007.
4 Charles P. Pfleeger, Shari Lawrence Pfleeger - Security in computing Third Edition - Prentice Hall of India 2006.
5 William Stallings, “Cryptography and Network security Principles and Practices”, Pearson/PHI, 5th ed, 2012.
Curriculum and Syllabus | M.E. Embedded System Technologies | R2019 Page 29