Page 1131 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 1131
One of the most common implementations of segregation of duties
policies is ensuring that security duties are separate from other duties
within an organization. In other words, personnel responsible for
auditing, monitoring, and reviewing security do not have other
operational duties related to what they are auditing, monitoring, and
reviewing. Whenever security duties are combined with other
operational duties, individuals can use their security privileges to
cover up activities related to their operational duties.
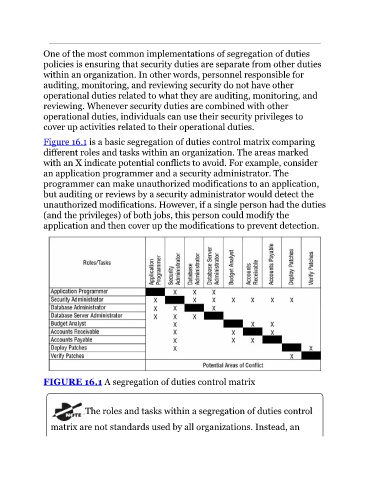
Figure 16.1 is a basic segregation of duties control matrix comparing
different roles and tasks within an organization. The areas marked
with an X indicate potential conflicts to avoid. For example, consider
an application programmer and a security administrator. The
programmer can make unauthorized modifications to an application,
but auditing or reviews by a security administrator would detect the
unauthorized modifications. However, if a single person had the duties
(and the privileges) of both jobs, this person could modify the
application and then cover up the modifications to prevent detection.
FIGURE 16.1 A segregation of duties control matrix
The roles and tasks within a segregation of duties control
matrix are not standards used by all organizations. Instead, an