Page 1188 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 1188
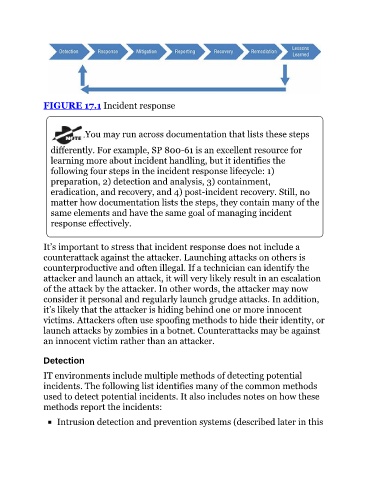
FIGURE 17.1 Incident response
You may run across documentation that lists these steps
differently. For example, SP 800-61 is an excellent resource for
learning more about incident handling, but it identifies the
following four steps in the incident response lifecycle: 1)
preparation, 2) detection and analysis, 3) containment,
eradication, and recovery, and 4) post-incident recovery. Still, no
matter how documentation lists the steps, they contain many of the
same elements and have the same goal of managing incident
response effectively.
It’s important to stress that incident response does not include a
counterattack against the attacker. Launching attacks on others is
counterproductive and often illegal. If a technician can identify the
attacker and launch an attack, it will very likely result in an escalation
of the attack by the attacker. In other words, the attacker may now
consider it personal and regularly launch grudge attacks. In addition,
it’s likely that the attacker is hiding behind one or more innocent
victims. Attackers often use spoofing methods to hide their identity, or
launch attacks by zombies in a botnet. Counterattacks may be against
an innocent victim rather than an attacker.
Detection
IT environments include multiple methods of detecting potential
incidents. The following list identifies many of the common methods
used to detect potential incidents. It also includes notes on how these
methods report the incidents:
Intrusion detection and prevention systems (described later in this