Page 1203 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 1203
chapter) are examples.
SYN Flood Attack
The SYN flood attack is a common DoS attack. It disrupts the
standard three-way handshake used by Transmission Control Protocol
(TCP) to initiate communication sessions. Normally, a client sends a
SYN (synchronize) packet to a server, the server responds with a
SYN/ACK (synchronize/acknowledge) packet to the client, and the
client then responds with an ACK (acknowledge) packet back to the
server. This three-way handshake establishes a communication
session that the two systems use for data transfer until the session is
terminated with FIN (finish) or RST (reset) packets.
However, in a SYN flood attack, the attackers send multiple SYN
packets but never complete the connection with an ACK. This is
similar to a jokester sticking his hand out to shake hands, but when
the other person sticks his hand out in response, the jokester pulls his
hand back, leaving the other person hanging.
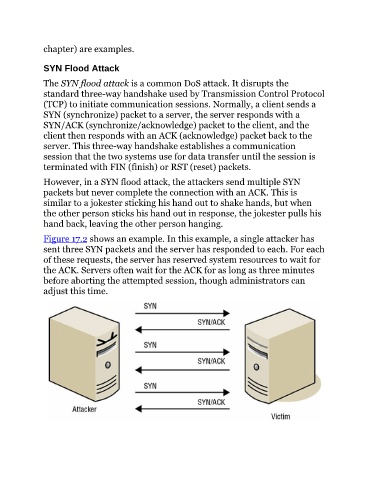
Figure 17.2 shows an example. In this example, a single attacker has
sent three SYN packets and the server has responded to each. For each
of these requests, the server has reserved system resources to wait for
the ACK. Servers often wait for the ACK for as long as three minutes
before aborting the attempted session, though administrators can
adjust this time.