Page 1211 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 1211
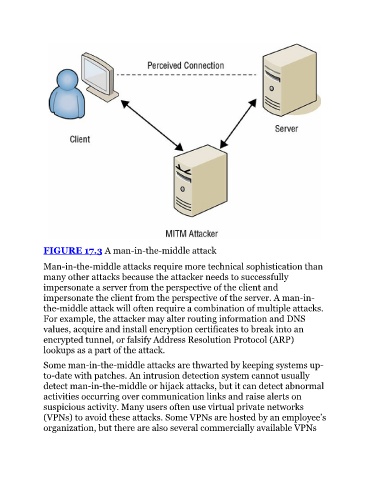
FIGURE 17.3 A man-in-the-middle attack
Man-in-the-middle attacks require more technical sophistication than
many other attacks because the attacker needs to successfully
impersonate a server from the perspective of the client and
impersonate the client from the perspective of the server. A man-in-
the-middle attack will often require a combination of multiple attacks.
For example, the attacker may alter routing information and DNS
values, acquire and install encryption certificates to break into an
encrypted tunnel, or falsify Address Resolution Protocol (ARP)
lookups as a part of the attack.
Some man-in-the-middle attacks are thwarted by keeping systems up-
to-date with patches. An intrusion detection system cannot usually
detect man-in-the-middle or hijack attacks, but it can detect abnormal
activities occurring over communication links and raise alerts on
suspicious activity. Many users often use virtual private networks
(VPNs) to avoid these attacks. Some VPNs are hosted by an employee’s
organization, but there are also several commercially available VPNs