Page 1222 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 1222
investigation is required to determine the actual source. This can be a
laborious process and is beyond the scope of the IDS. However, it is
possible to discover the source of spoofed IPs with some investigation.
It is unethical and risky to launch counterstrikes against
an intruder or to attempt to reverse-hack an intruder’s computer
system. Instead, rely on your logging capabilities and sniffing
collections to provide sufficient data to prosecute criminals or to
improve the security of your environment in response.
A NIDS is usually able to detect the initiation of an attack or ongoing
attacks, but it can’t always provide information about the success of an
attack. It won’t know if an attack affected specific systems, user
accounts, files, or applications. For example, a NIDS may discover that
a buffer overflow exploit was sent through the network, but it won’t
necessarily know whether the exploit successfully infiltrated a system.
However, after administrators receive the alert they can check relevant
systems. Additionally, investigators can use the NIDS logs as part of an
audit trail to learn what happened.
Intrusion Prevention Systems
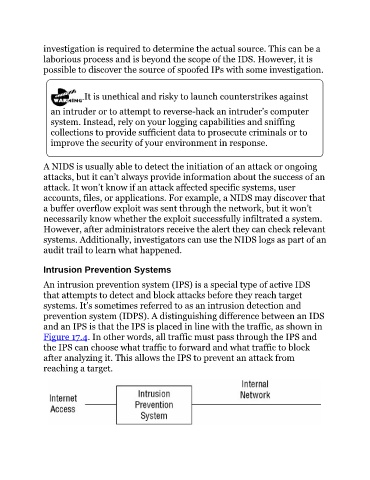
An intrusion prevention system (IPS) is a special type of active IDS
that attempts to detect and block attacks before they reach target
systems. It’s sometimes referred to as an intrusion detection and
prevention system (IDPS). A distinguishing difference between an IDS
and an IPS is that the IPS is placed in line with the traffic, as shown in
Figure 17.4. In other words, all traffic must pass through the IPS and
the IPS can choose what traffic to forward and what traffic to block
after analyzing it. This allows the IPS to prevent an attack from
reaching a target.