Page 456 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 456
detect the copy and (if uniquely watermarked files are provided to
each original recipient) trace the offending copy back to the source.
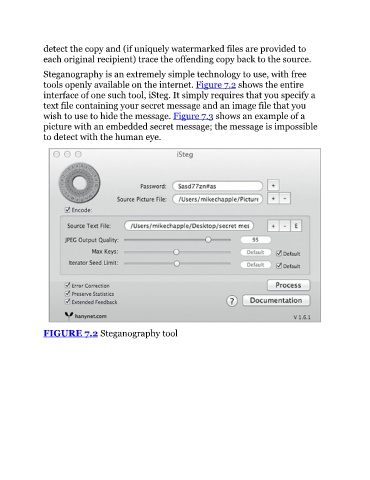
Steganography is an extremely simple technology to use, with free
tools openly available on the internet. Figure 7.2 shows the entire
interface of one such tool, iSteg. It simply requires that you specify a
text file containing your secret message and an image file that you
wish to use to hide the message. Figure 7.3 shows an example of a
picture with an embedded secret message; the message is impossible
to detect with the human eye.
FIGURE 7.2 Steganography tool