Page 494 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 494
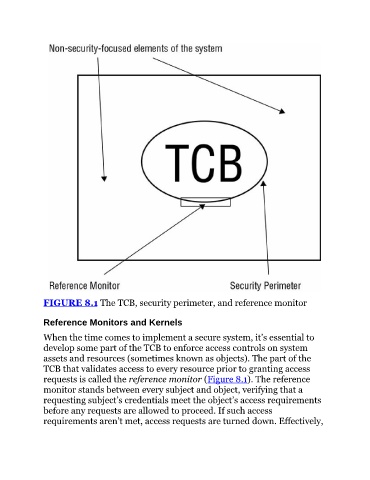
FIGURE 8.1 The TCB, security perimeter, and reference monitor
Reference Monitors and Kernels
When the time comes to implement a secure system, it’s essential to
develop some part of the TCB to enforce access controls on system
assets and resources (sometimes known as objects). The part of the
TCB that validates access to every resource prior to granting access
requests is called the reference monitor (Figure 8.1). The reference
monitor stands between every subject and object, verifying that a
requesting subject’s credentials meet the object’s access requirements
before any requests are allowed to proceed. If such access
requirements aren’t met, access requests are turned down. Effectively,