Page 127 - Towards Trustworthy Elections New Directions in Electronic Voting by Ed Gerck (auth.), David Chaum, Markus Jakobsson, Ronald L. Rivest, Peter Y. A. Ryan, Josh Benaloh, Miroslaw Kutylowski, Ben Adida ( (z-lib.org (1)
P. 127
Unconditionally Secure Electronic Voting
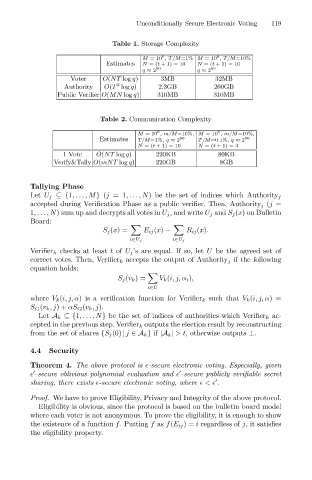
Table 1. Storage Complexity
6
M =10 , T/M=1% M =10 , T/M=10%
Estimates
N =(t +1) = 10
80
80 6 N =(t +1) = 10 119
q ≈ 2 q ≈ 2
Voter O(NT log q) 3MB 32MB
2
Authority O(T log q) 2.3GB 200GB
Public Verifier O(MN log q) 310MB 310MB
Table 2. Communication Complexity
6 6
M =10 , m/M=10%, M =10 , m/M=10%,
Estimates T/M=1%, q ≈ 2 80 T/M=0.1%, q ≈ 2 80
N =(t +1) = 10 N =(t +1) = 3
1Vote O(NT log q) 220KB 80KB
Verify&Tally O(mNT log q) 220GB 8GB
Tallying Phase
Let U j ⊆{1,... ,M} (j =1,... ,N) be the set of indices which Authority j
accepted during Verification Phase as a public verifier. Then, Authority j (j =
1,... ,N) sum up and decrypts all votes in U j ,and write U j and S j (x) on Bulletin
Board:
S j (x)= E ij (x) − R ij (x).
i∈U j i∈U j
Verifier k checks at least t of U j ’s are equal. If so, let U be the agreed set of
correct votes. Then, Verifier k accepts the output of Authority j if the following
equation holds:
S j (v k )= V k (i, j, α i ),
i∈U
where V k (i, j, α) is a verification function for Verifier k such that V k (i, j, α)=
S i1 (v k ,j)+ αS i2 (v k ,j).
Let A k ⊆{1,... ,N} be the set of indices of authorities which Verifier k ac-
cepted in the previous step. Verifier k outputs the election result by reconstructing
from the set of shares {S j (0) | j ∈A k } if |A k | >t, otherwise outputs ⊥.
4.4 Security
Theorem 4. The above protocol is -secure electronic voting. Especially, given
-secure oblivious polynomial evaluation and -secure publicly verifiable secret
sharing, there exists -secure electronic voting, where < .
Proof. We have to prove Eligibility, Privacy and Integrity of the above protocol.
Eligibility is obvious, since the protocol is based on the bulletin board model
where each voter is not anonymous. To prove the eligibility, it is enough to show
the existence of a function f. Putting f as f(E ij )= i regardless of j,it satisfies
the eligibility property.