Page 1020 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 1020
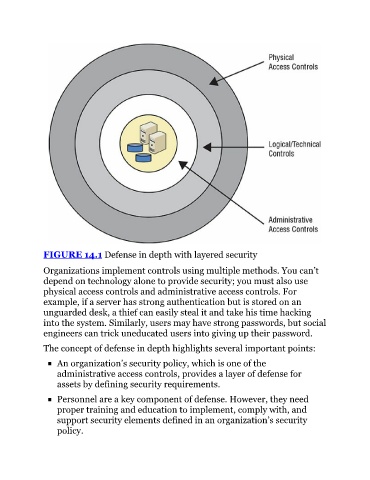
FIGURE 14.1 Defense in depth with layered security
Organizations implement controls using multiple methods. You can’t
depend on technology alone to provide security; you must also use
physical access controls and administrative access controls. For
example, if a server has strong authentication but is stored on an
unguarded desk, a thief can easily steal it and take his time hacking
into the system. Similarly, users may have strong passwords, but social
engineers can trick uneducated users into giving up their password.
The concept of defense in depth highlights several important points:
An organization’s security policy, which is one of the
administrative access controls, provides a layer of defense for
assets by defining security requirements.
Personnel are a key component of defense. However, they need
proper training and education to implement, comply with, and
support security elements defined in an organization’s security
policy.