Page 1024 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 1024
assigned tasks. Role Based Access Control (RBAC) is often
implemented using groups.
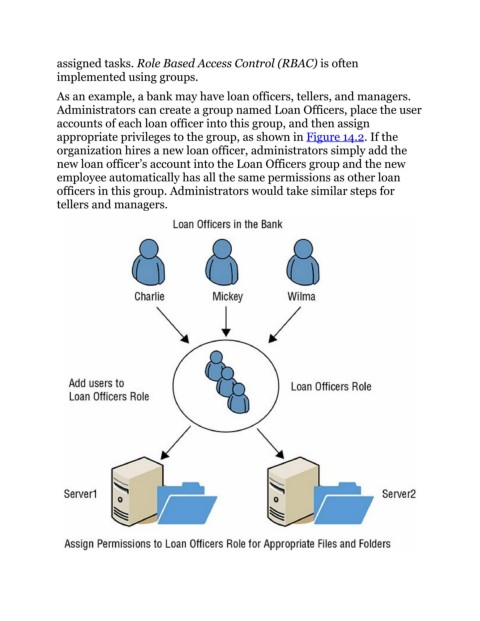
As an example, a bank may have loan officers, tellers, and managers.
Administrators can create a group named Loan Officers, place the user
accounts of each loan officer into this group, and then assign
appropriate privileges to the group, as shown in Figure 14.2. If the
organization hires a new loan officer, administrators simply add the
new loan officer’s account into the Loan Officers group and the new
employee automatically has all the same permissions as other loan
officers in this group. Administrators would take similar steps for
tellers and managers.