Page 1029 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 1029
Users have labels assigned to them based on their clearance level,
which is a form of privilege. Similarly, objects have labels, which
indicate their level of classification or sensitivity. For example, the
U.S. military uses the labels of Top Secret, Secret, and Confidential to
classify data. Administrators can grant access to Top Secret data to
users with Top Secret clearances. However, administrators cannot
grant access to Top Secret data to users with lower-level clearances
such as Secret and Confidential.
Organizations in the private sector often use labels such as
confidential (or proprietary), private, sensitive, and public. While
governments use labels mandated by law, private sector organizations
are free to use whatever labels they choose.
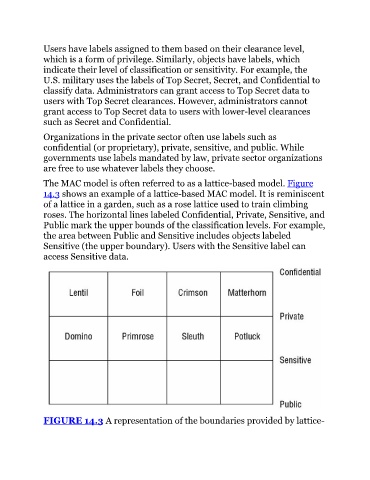
The MAC model is often referred to as a lattice-based model. Figure
14.3 shows an example of a lattice-based MAC model. It is reminiscent
of a lattice in a garden, such as a rose lattice used to train climbing
roses. The horizontal lines labeled Confidential, Private, Sensitive, and
Public mark the upper bounds of the classification levels. For example,
the area between Public and Sensitive includes objects labeled
Sensitive (the upper boundary). Users with the Sensitive label can
access Sensitive data.
FIGURE 14.3 A representation of the boundaries provided by lattice-