Page 115 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 115
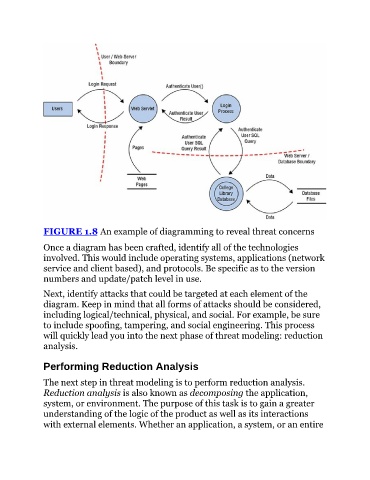
FIGURE 1.8 An example of diagramming to reveal threat concerns
Once a diagram has been crafted, identify all of the technologies
involved. This would include operating systems, applications (network
service and client based), and protocols. Be specific as to the version
numbers and update/patch level in use.
Next, identify attacks that could be targeted at each element of the
diagram. Keep in mind that all forms of attacks should be considered,
including logical/technical, physical, and social. For example, be sure
to include spoofing, tampering, and social engineering. This process
will quickly lead you into the next phase of threat modeling: reduction
analysis.
Performing Reduction Analysis
The next step in threat modeling is to perform reduction analysis.
Reduction analysis is also known as decomposing the application,
system, or environment. The purpose of this task is to gain a greater
understanding of the logic of the product as well as its interactions
with external elements. Whether an application, a system, or an entire