Page 1488 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 1488
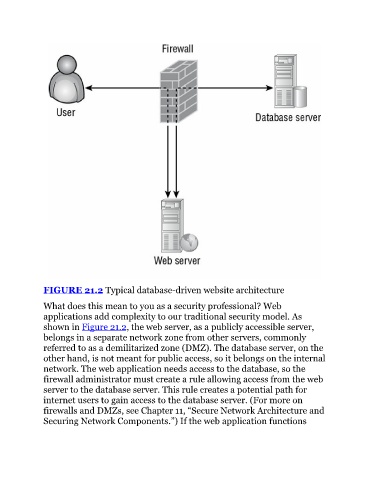
FIGURE 21.2 Typical database-driven website architecture
What does this mean to you as a security professional? Web
applications add complexity to our traditional security model. As
shown in Figure 21.2, the web server, as a publicly accessible server,
belongs in a separate network zone from other servers, commonly
referred to as a demilitarized zone (DMZ). The database server, on the
other hand, is not meant for public access, so it belongs on the internal
network. The web application needs access to the database, so the
firewall administrator must create a rule allowing access from the web
server to the database server. This rule creates a potential path for
internet users to gain access to the database server. (For more on
firewalls and DMZs, see Chapter 11, “Secure Network Architecture and
Securing Network Components.”) If the web application functions