Page 163 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 163
organization’s infrastructure through the circumvention of security
controls and is able to directly imperil assets.
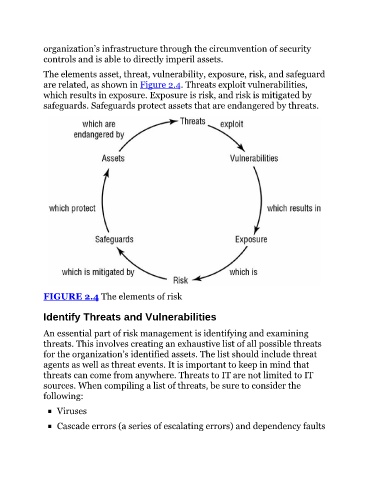
The elements asset, threat, vulnerability, exposure, risk, and safeguard
are related, as shown in Figure 2.4. Threats exploit vulnerabilities,
which results in exposure. Exposure is risk, and risk is mitigated by
safeguards. Safeguards protect assets that are endangered by threats.
FIGURE 2.4 The elements of risk
Identify Threats and Vulnerabilities
An essential part of risk management is identifying and examining
threats. This involves creating an exhaustive list of all possible threats
for the organization’s identified assets. The list should include threat
agents as well as threat events. It is important to keep in mind that
threats can come from anywhere. Threats to IT are not limited to IT
sources. When compiling a list of threats, be sure to consider the
following:
Viruses
Cascade errors (a series of escalating errors) and dependency faults