Page 181 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 181
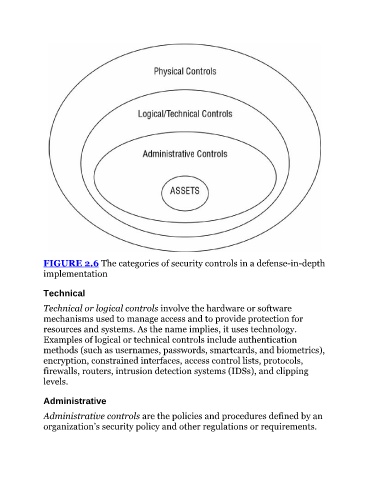
FIGURE 2.6 The categories of security controls in a defense-in-depth
implementation
Technical
Technical or logical controls involve the hardware or software
mechanisms used to manage access and to provide protection for
resources and systems. As the name implies, it uses technology.
Examples of logical or technical controls include authentication
methods (such as usernames, passwords, smartcards, and biometrics),
encryption, constrained interfaces, access control lists, protocols,
firewalls, routers, intrusion detection systems (IDSs), and clipping
levels.
Administrative
Administrative controls are the policies and procedures defined by an
organization’s security policy and other regulations or requirements.