Page 176 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 176
department, division, office, or branch.
Delphi Technique
The Delphi technique is probably the only mechanism on the previous
list that is not immediately recognizable and understood. The Delphi
technique is simply an anonymous feedback-and-response process
used to enable a group to reach an anonymous consensus. Its primary
purpose is to elicit honest and uninfluenced responses from all
participants. The participants are usually gathered into a single
meeting room. To each request for feedback, each participant writes
down their response on paper anonymously. The results are compiled
and presented to the group for evaluation. The process is repeated
until a consensus is reached.
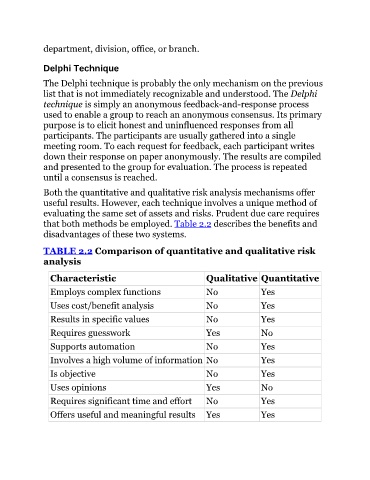
Both the quantitative and qualitative risk analysis mechanisms offer
useful results. However, each technique involves a unique method of
evaluating the same set of assets and risks. Prudent due care requires
that both methods be employed. Table 2.2 describes the benefits and
disadvantages of these two systems.
TABLE 2.2 Comparison of quantitative and qualitative risk
analysis
Characteristic Qualitative Quantitative
Employs complex functions No Yes
Uses cost/benefit analysis No Yes
Results in specific values No Yes
Requires guesswork Yes No
Supports automation No Yes
Involves a high volume of information No Yes
Is objective No Yes
Uses opinions Yes No
Requires significant time and effort No Yes
Offers useful and meaningful results Yes Yes