Page 318 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 318
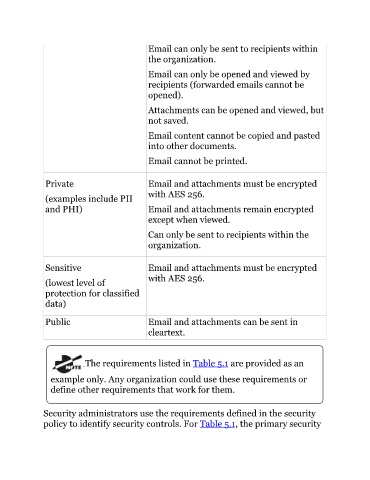
Email can only be sent to recipients within
the organization.
Email can only be opened and viewed by
recipients (forwarded emails cannot be
opened).
Attachments can be opened and viewed, but
not saved.
Email content cannot be copied and pasted
into other documents.
Email cannot be printed.
Private Email and attachments must be encrypted
with AES 256.
(examples include PII
and PHI) Email and attachments remain encrypted
except when viewed.
Can only be sent to recipients within the
organization.
Sensitive Email and attachments must be encrypted
with AES 256.
(lowest level of
protection for classified
data)
Public Email and attachments can be sent in
cleartext.
The requirements listed in Table 5.1 are provided as an
example only. Any organization could use these requirements or
define other requirements that work for them.
Security administrators use the requirements defined in the security
policy to identify security controls. For Table 5.1, the primary security