Page 425 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 425
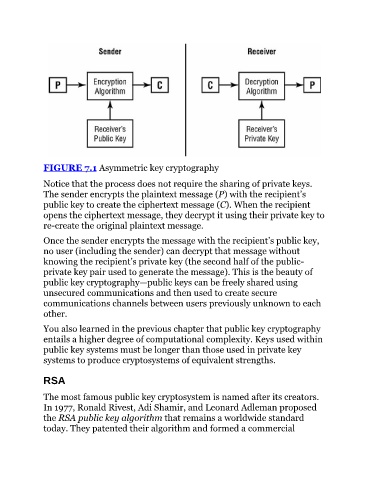
FIGURE 7.1 Asymmetric key cryptography
Notice that the process does not require the sharing of private keys.
The sender encrypts the plaintext message (P) with the recipient’s
public key to create the ciphertext message (C). When the recipient
opens the ciphertext message, they decrypt it using their private key to
re-create the original plaintext message.
Once the sender encrypts the message with the recipient’s public key,
no user (including the sender) can decrypt that message without
knowing the recipient’s private key (the second half of the public-
private key pair used to generate the message). This is the beauty of
public key cryptography—public keys can be freely shared using
unsecured communications and then used to create secure
communications channels between users previously unknown to each
other.
You also learned in the previous chapter that public key cryptography
entails a higher degree of computational complexity. Keys used within
public key systems must be longer than those used in private key
systems to produce cryptosystems of equivalent strengths.
RSA
The most famous public key cryptosystem is named after its creators.
In 1977, Ronald Rivest, Adi Shamir, and Leonard Adleman proposed
the RSA public key algorithm that remains a worldwide standard
today. They patented their algorithm and formed a commercial