Page 101 - Towards Trustworthy Elections New Directions in Electronic Voting by Ed Gerck (auth.), David Chaum, Markus Jakobsson, Ronald L. Rivest, Peter Y. A. Ryan, Josh Benaloh, Miroslaw Kutylowski, Ben Adida ( (z-lib.org (1)
P. 101
93
A Secure Architecture for Voting Electronically (SAVE)
In the case of current electronic voting systems, there is a single direct line from
the voter to the ballot storage device to the aggregator. Each of these systems
has a failure probability, and the communication channels between them also
have the ability to be compromised. This model of the current electronic voting
system can be represented in Equation 2. For the entire stage to fail, there
can be failures in up to t modules. For each number of failures f,we have the
n
combination of possible failures in various modules. For each of those, we
f
compute the probability of each number of failures f that result in a valid result.
To ensure the elimination of common potential vulnerabilities, the source code
for each system will be passed through a commonality checker such as PLAG or
SMAT [25,29]. This system tests for similarities between code, and is commonly
used to detect cheating in assignments. In addition to the source code, it is
prudent to examine the compiler used and in fact, varying the actual compilers
used aids in preventing the external introduction of common vulnerabilities.
The use of common components on the SAVE system can be modeled by
starting with the threshold failure model and collapsing the number of (effec-
tively) independent modules. Then, the threshold equation reduces the effective
number of components, resulting in an strictly higher probability of failure than
any system with full diversity.
Adding the communication channel into the mix adds another product factor
into each possible failure rate but does not fundamentally change the equation.
Using a common communication channel (the most likely scenario) between
components (e.g. ethernet) simply adds a common term shown in Equation 3.
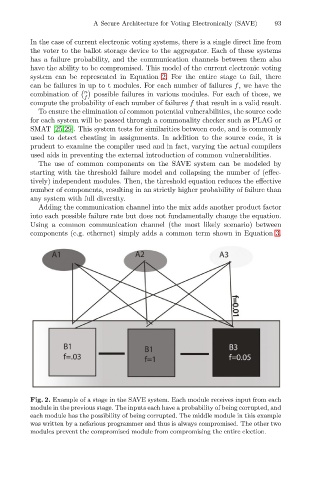
Fig. 2. Example of a stage in the SAVE system. Each module receives input from each
module in the previous stage. The inputs each have a probability of being corrupted, and
each module has the possibility of being corrupted. The middle module in this example
was written by a nefarious programmer and thus is always compromised. The other two
modules prevent the compromised module from compromising the entire election.