Page 252 - Towards Trustworthy Elections New Directions in Electronic Voting by Ed Gerck (auth.), David Chaum, Markus Jakobsson, Ronald L. Rivest, Peter Y. A. Ryan, Josh Benaloh, Miroslaw Kutylowski, Ben Adida ( (z-lib.org (1)
P. 252
244
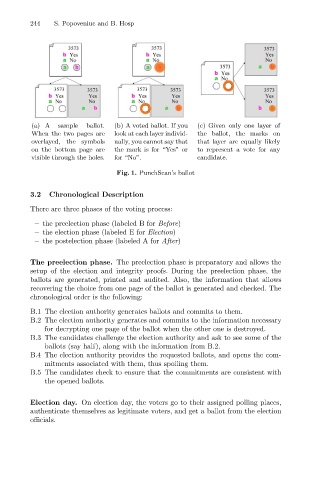
sample
(a) A S. Popoveniuc and B. Hosp (c) Given only one layer of
(b) A voted ballot. If you
ballot.
When the two pages are look at each layer individ- the ballot, the marks on
overlayed, the symbols ually, you cannot say that that layer are equally likely
on the bottom page are the mark is for “Yes” or to represent a vote for any
visible through the holes. for “No”. candidate.
Fig. 1. PunchScan’s ballot
3.2 Chronological Description
There are three phases of the voting process:
– the preelection phase (labeled B for Before)
– the election phase (labeled E for Election)
– the postelection phase (labeled A for After)
The preelection phase. The preelection phase is preparatory and allows the
setup of the election and integrity proofs. During the preelection phase, the
ballots are generated, printed and audited. Also, the information that allows
recovering the choice from one page of the ballot is generated and checked. The
chronological order is the following:
B.1 The election authority generates ballots and commits to them.
B.2 The election authority generates and commits to the information necessary
for decrypting one page of the ballot when the other one is destroyed.
B.3 The candidates challenge the election authority and ask to see some of the
ballots (say half), along with the information from B.2.
B.4 The election authority provides the requested ballots, and opens the com-
mitments associated with them, thus spoiling them.
B.5 The candidates check to ensure that the commitments are consistent with
the opened ballots.
Election day. On election day, the voters go to their assigned polling places,
authenticate themselves as legitimate voters, and get a ballot from the election
officials.