Page 1090 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 1090
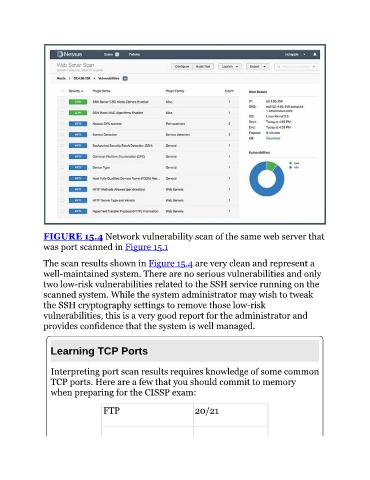
FIGURE 15.4 Network vulnerability scan of the same web server that
was port scanned in Figure 15.1
The scan results shown in Figure 15.4 are very clean and represent a
well-maintained system. There are no serious vulnerabilities and only
two low-risk vulnerabilities related to the SSH service running on the
scanned system. While the system administrator may wish to tweak
the SSH cryptography settings to remove those low-risk
vulnerabilities, this is a very good report for the administrator and
provides confidence that the system is well managed.
Learning TCP Ports
Interpreting port scan results requires knowledge of some common
TCP ports. Here are a few that you should commit to memory
when preparing for the CISSP exam:
FTP 20/21