Page 505 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 505
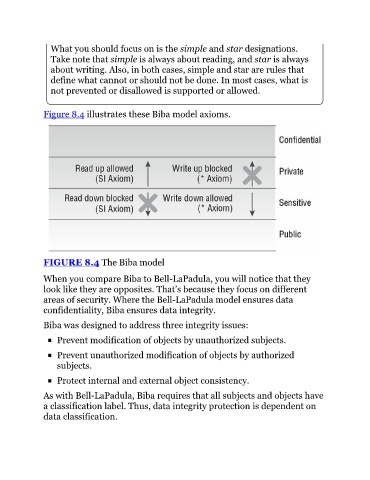
What you should focus on is the simple and star designations.
Take note that simple is always about reading, and star is always
about writing. Also, in both cases, simple and star are rules that
define what cannot or should not be done. In most cases, what is
not prevented or disallowed is supported or allowed.
Figure 8.4 illustrates these Biba model axioms.
FIGURE 8.4 The Biba model
When you compare Biba to Bell-LaPadula, you will notice that they
look like they are opposites. That’s because they focus on different
areas of security. Where the Bell-LaPadula model ensures data
confidentiality, Biba ensures data integrity.
Biba was designed to address three integrity issues:
Prevent modification of objects by unauthorized subjects.
Prevent unauthorized modification of objects by authorized
subjects.
Protect internal and external object consistency.
As with Bell-LaPadula, Biba requires that all subjects and objects have
a classification label. Thus, data integrity protection is dependent on
data classification.