Page 757 - (ISC)² CISSP Certified Information Systems Security Professional Official Study Guide
P. 757
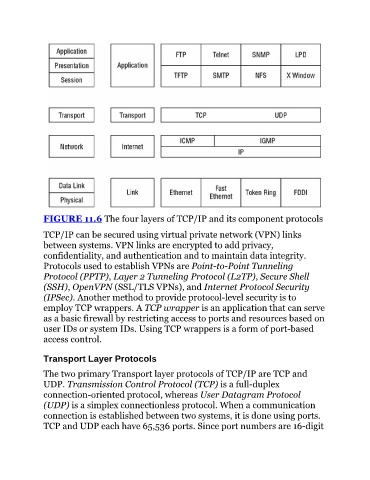
FIGURE 11.6 The four layers of TCP/IP and its component protocols
TCP/IP can be secured using virtual private network (VPN) links
between systems. VPN links are encrypted to add privacy,
confidentiality, and authentication and to maintain data integrity.
Protocols used to establish VPNs are Point-to-Point Tunneling
Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), Secure Shell
(SSH), OpenVPN (SSL/TLS VPNs), and Internet Protocol Security
(IPSec). Another method to provide protocol-level security is to
employ TCP wrappers. A TCP wrapper is an application that can serve
as a basic firewall by restricting access to ports and resources based on
user IDs or system IDs. Using TCP wrappers is a form of port-based
access control.
Transport Layer Protocols
The two primary Transport layer protocols of TCP/IP are TCP and
UDP. Transmission Control Protocol (TCP) is a full-duplex
connection-oriented protocol, whereas User Datagram Protocol
(UDP) is a simplex connectionless protocol. When a communication
connection is established between two systems, it is done using ports.
TCP and UDP each have 65,536 ports. Since port numbers are 16-digit